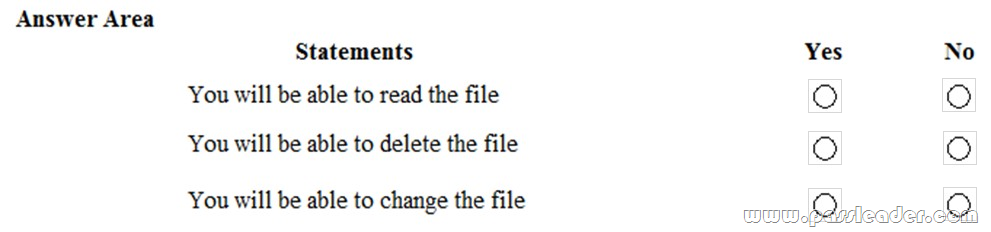
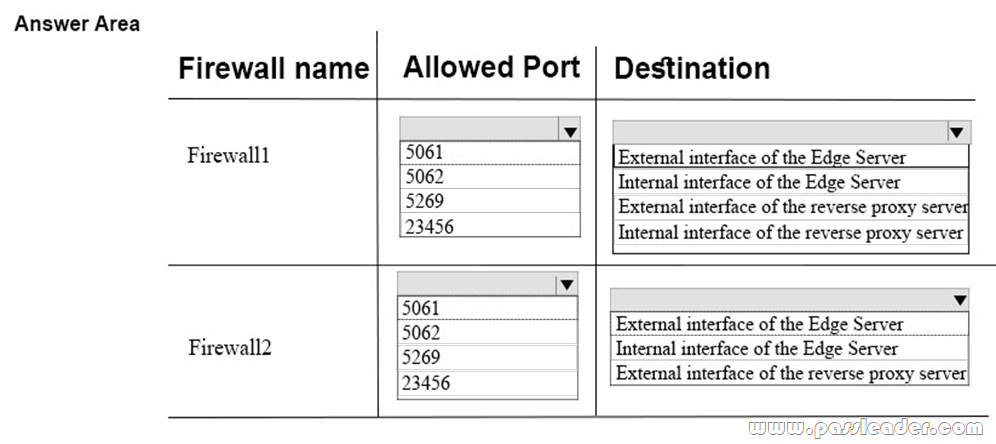
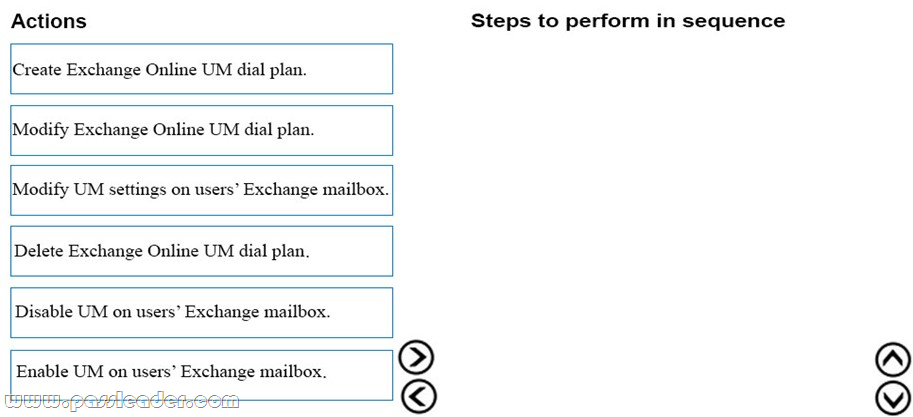
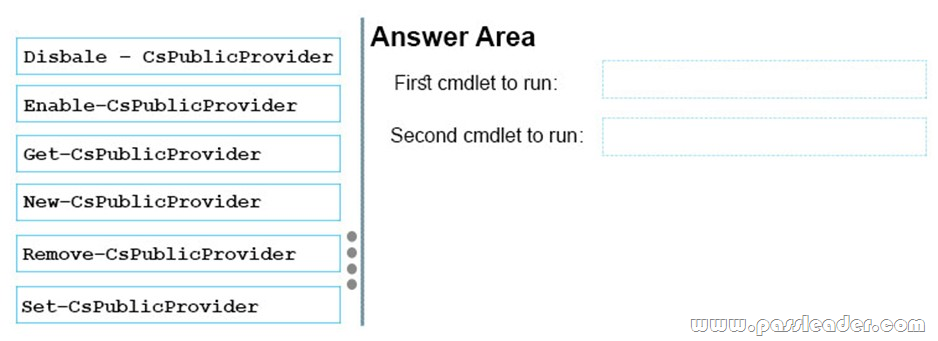
New Updated AZ-103 Exam Questions from PassLeader AZ-103 PDF dumps! Welcome to download the newest PassLeader AZ-103 VCE dumps: https://www.passleader.com/az-103.html (250 Q&As)
Keywords: AZ-103 exam dumps, AZ-103 exam questions, AZ-103 VCE dumps, AZ-103 PDF dumps, AZ-103 practice tests, AZ-103 study guide, AZ-103 braindumps, Microsoft Azure Administrator Exam
P.S. New AZ-103 dumps PDF: https://drive.google.com/open?id=1pcJSvWksUYfrmRT5Hy9xnh0iGBvW_sfq
P.S. New AZ-102 dumps PDF: https://drive.google.com/open?id=1HceOeaJ6TUh6408k3UU7gZb7aXGzzGb–
NEW QUESTION 1
You have an Azure subscription that contains 100 virtual machines. You regularly create and delete virtual machines. You need to identify unused disks that can be deleted. What should you do?
A. From Microsoft Azure Storage Explorer, view the Account Management properties.
B. From the Azure portal, configure the Advisor recommendations.
C. From Cloudyn, open the Optimizer tab and create a report.
D. From Cloudyn, create a Cost Management report.
Answer: C
Explanation:
The Unattached Disks report lists storage that is not attached to any active VM. To open the report, click in the Optimizer tab. Select Inefficiencies and the click Unattached Disks.
https://social.msdn.microsoft.com/Forums/en-US/0e4b3c28-a7f3-416b-84b7-3753f534e1b9/faq-how-to-save-money-with-cloudyn-8211-10-steps?forum=Cloudyn
https://docs.microsoft.com/en-us/azure/cost-management/overview
NEW QUESTION 2
You plan to automate the deployment of a virtual machine scale set that uses the Windows Server 2016 Datacenter image. You need to ensure that when the scale set virtual machines are provisioned, they have web server components installed. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Modify the extensionProfile section of the Azure Resource Manager template.
B. Create a new virtual machine scale set in the Azure portal.
C. Create an Azure policy.
D. Create an automation account.
E. Upload a configuration script.
Answer: AB
Explanation:
Virtual Machine Scale Sets can be used with the Azure Desired State Configuration (DSC) extension handler. Virtual machine scale sets provide a way to deploy and manage large numbers of virtual machines, and can elastically scale in and out in response to load. DSC is used to configure the VMs as they come online so they are running the production software.
https://docs.microsoft.com/en-us/azure/virtual-machine-scale-sets/virtual-machine-scale-sets-dsc
NEW QUESTION 3
Your company has an Azure subscription named Subscription1. The company also has two on-premises servers named Server1 and Server2 that run Windows Server 2016. Server1 is configured as a DNS server that has a primary DNS zone named adatum.com. Adatum.com contains 1,000 DNS records. You manage Server1 and Subscription1 from Server2. Server2 has the following tools installed:
– The DNS Manager console
– Azure PowerShell
– Azure CLI 2.0
You need to move the adatum.com zone to Subscription1. The solution must minimize administrative effort. What should you use?
A. The Azure PowerShell
B. The Azure CLI
C. The Azure Portal
D. The DNS Manager Console
Answer: B
Explanation:
Azure DNS supports importing and exporting zone files by using the Azure command-line interface (CLI). Zone file import is not currently supported via Azure PowerShell or the Azure portal.
https://docs.microsoft.com/en-us/azure/dns/dns-import-export
NEW QUESTION 4
You have an Azure Active Directory (Azure AD) tenant named contosocloud.onmicrosoft.com. Your company has a public DNS zone for contoso.com. You add contoso.com as a custom domain name to Azure AD. You need to ensure that Azure can verify the domain name. Which type of DNS record should you create?
A. RRSIG
B. PTR
C. DNSKEY
D. TXT
Answer: D
Explanation:
Create the TXT record. App Services uses this record only at configuration time to verify that you own the custom domain. You can delete this TXT record after your custom domain is validated and configured in App Service.
https://docs.microsoft.com/en-us/azure/dns/dns-web-sites-custom-domain
NEW QUESTION 5
You have an Azure virtual machine named VM1. VM1 was deployed by using a custom Azure Resource Manager template named ARM1.json. You receive a notification that VM1 will be affected by maintenance. You need to move VM1 to a different host immediately.
Solution: Solution: From the Overview blade, you move the virtual machine to a different subscription.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
You would need to Redeploy the VM.
https://docs.microsoft.com/en-us/azure/virtual-machines/troubleshooting/redeploy-to-new-node-windows
NEW QUESTION 6
You have a resource group named RG1. RG1 contains an Azure Storage account named storageaccount1 and a virtual machine named VM1 that runs Windows Server 2016. Storageaccount1 contains the disk files for VM1. You apply a ReadOnly lock to RG1. What can you do from the Azure portal?
A. Generate an automation script for RG1.
B. View the keys of storageaccount1.
C. Upload a blob to storageaccount1.
D. Start VM1.
Answer: B
Explanation:
ReadOnly means authorized users can read a resource, but they can’t delete or update the resource. Applying this lock is similar to restricting all authorized users to the permissions granted by the Reader role.
https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources
NEW QUESTION 7
You have an Azure subscription that contains 10 virtual networks. The virtual networks are hosted in separate resource groups. Another administrator plans to create several network security groups (NSGs) in the subscription. You need to ensure that when an NSG is created, it automatically blocks TCP port 8080 between the virtual networks.
Solution: You assign a built-in policy definition to the subscription.
Does this meet the goal?
A. Yes
B. No
Answer: B
NEW QUESTION 8
You have an Azure subscription that contains a resource group named RG1. RG1 contains 100 virtual machines. Your company has three cost centers named Manufacturing, Sales, and Finance. You need to associate each virtual machine to a specific cost center. What should you do?
A. Add an extension to the virtual machines.
B. Modify the inventory settings of the virtual machine.
C. Assign tags to the virtual machines.
D. Configure locks for the virtual machine.
Answer: C
Explanation:
https://docs.microsoft.com/en-us/azure/billing/billing-getting-started
https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-using-tags
NEW QUESTION 9
You have an Azure subscription named Subscription1. You have 5 TB of data that you need to transfer to Subscription. You plan to use an Azure Import/Export job. What can you use as the destination of the imported data?
A. Azure SQL Database
B. Azure Data Factory
C. A Virtual Machine
D. Azure Blob Storage
Answer: D
Explanation:
https://docs.microsoft.com/en-us/azure/storage/common/storage-import-export-service
NEW QUESTION 10
You plan to back up an Azure virtual machine named VM1. You discover that the Backup Pre-Check status displays a status of Warning. What is a possible cause of the Warning status?
A. VM1 does not have the latest version of WaAppAgent.exe installed.
B. VM1 has an unmanaged disk.
C. VM1 is stopped.
D. A Recovery Services vault is unavailable.
Answer: A
Explanation:
The Warning state indicates one or more issues in VM’s configuration that might lead to backup failures and provides recommended steps to ensure successful backups. Not having the latest VM Agent installed, for example, can cause backups to fail intermittently and falls in this class of issues.
https://azure.microsoft.com/en-us/blog/azure-vm-backup-pre-checks/
NEW QUESTION 11
You have an Azure subscription that contains three virtual networks named VNet1, VNet2, VNet3. VNet2 contains a virtual appliance named VM2 that operates as a router. You are configuring the virtual networks in a hub and spoke topology that uses VNet2 as the hub network. You plan to configure peering between VNet1 and VNet2 and between VNet2 and VNet3. You need to provide connectivity between VNet1 and VNet3 through VNet2. Which two configurations should you perform? (Each correct answer presents part of the solution. Choose two.)
A. On the peering connections, allow forwarded traffic.
B. On the peering connections, allow gateway transit.
C. Create route tables and assign the table to subnets.
D. Create a route filter.
E. On the peering connections, use remote gateways.
Answer: BE
Explanation:
Allow gateway transit: Check this box if you have a virtual network gateway attached to this virtual network and want to allow traffic from the peered virtual network to flow through the gateway. The peered virtual network must have the Use remote gateways checkbox checked when setting up the peering from the other virtual network to this virtual network.
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-manage-peering#requirements-and-constraints
NEW QUESTION 12
You have an Azure web app named Appl. App1 runs in an Azure App Service plan named Plan1. Plan1 is associated to the Free pricing tier. You discover that App1 stops each day after running continuously for 60 minutes. You need to ensure that App1 can run continuously for the entire day.
Solution: You change the pricing tier of Plan1 to Basic.
Does this meet the goal?
A. Yes
B. No
Answer: A
Explanation:
The Free Tier provides 60 CPU minutes/day. This explains why App1 is stops. The Basic tier has no such cap.
https://azure.microsoft.com/en-us/pricing/details/app-service/windows/
NEW QUESTION 13
You have an Azure Active Directory (Azure AD) tenant named Adatum and an Azure Subscription named Subscription1. Adatum contains a group named Developers. Subscription1 contains a resource group named Dev. You need to provide the Developers group with the ability to create Azure logic apps in the Dev resource group.
Solution: On Subscription1, you assign the DevTest Labs User role to the Developers group.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
DevTest Labs User role only lets you connect, start, restart, and shutdown virtual machines in your Azure DevTest Labs. You would need the Logic App Contributor role.
https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles
https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-securing-a-logic-app
NEW QUESTION 14
You are building a custom Azure function app to connect to Azure Event Grid. You need to ensure that resources are allocated dynamically to the function app. Billing must be based on the executions of the app. What should you configure when you create the function app?
A. The Windows operating system and the Consumption plan hosting plan.
B. The Windows operating system and the App Service plan hosting plan.
C. The Docker container and an App Service plan that uses the B1 pricing tier.
D. The Docker container and an App Service plan that uses the S1 pricing tier.
Answer: A
Explanation:
Azure Functions runs in two different modes: Consumption plan and Azure App Service plan. The Consumption plan automatically allocates compute power when your code is running. Your app is scaled out when needed to handle load, and scaled down when code is not running.
Incorrect:
Not B: When you run in an App Service plan, you must manage the scaling of your function app.
https://docs.microsoft.com/en-us/azure/azure-functions/functions-create-first-azure-function
NEW QUESTION 15
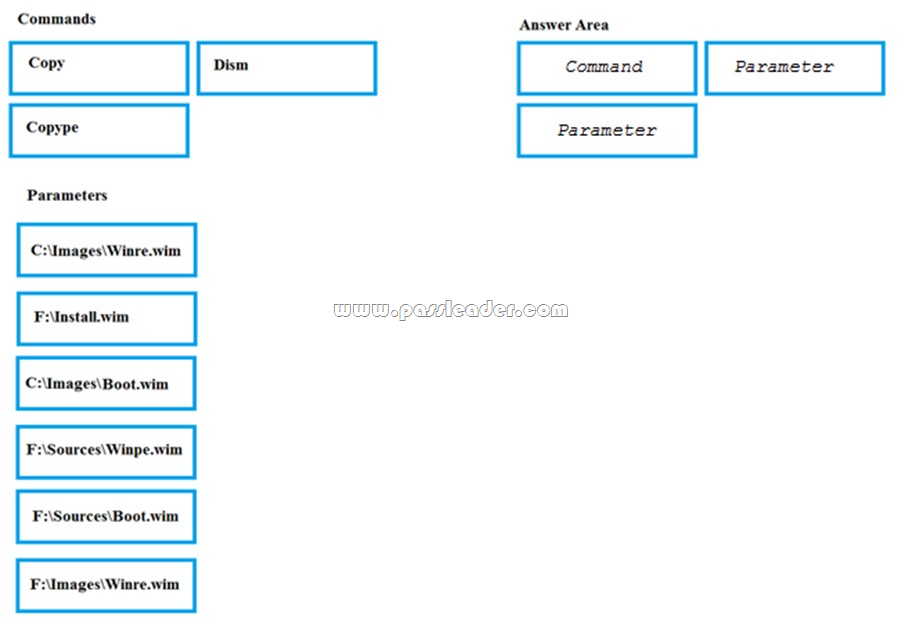
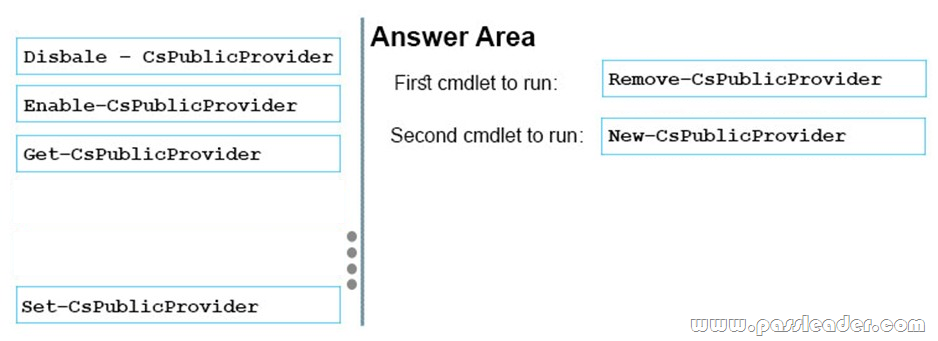
Drag and Drop
You have an Azure subscription that contains the following resources:
– a virtual network named VNet1
– a replication policy named ReplPolicy1
– a Recovery Services vault named Vault1
– an Azure Storage account named Storage1
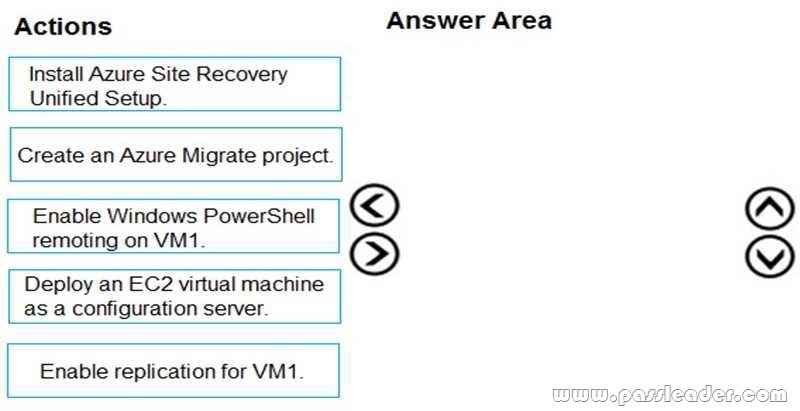
You have an Amazon Web Services (AWS) EC2 virtual machine named VM1 that runs Windows Server. You need to migrate VM1 to VNet1 by using Azure Site Recovery. Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
![]()
Answer:
![]()
Explanation:
Step 1: Deploy an EC2 virtual machine as a configuration server Prepare source include:
1. Use an EC2 instance that’s running Windows Server 2012 R2 to create a configuration server and register it with your recovery vault.
2. Configure the proxy on the EC2 instance VM you’re using as the configuration server so that it can access the service URLs.
Step 2: Install Azure Site Recovery Unified Setup. Download Microsoft Azure Site Recovery Unified Setup. You can download it to your local machine and then copy it to the VM you’re using as the configuration server.
Step 3: Enable replication for VM1. Enable replication for each VM that you want to migrate. When replication is enabled, Site Recovery automatically installs the Mobility service.
https://docs.microsoft.com/en-us/azure/site-recovery/migrate-tutorial-aws-azure
NEW QUESTION 16
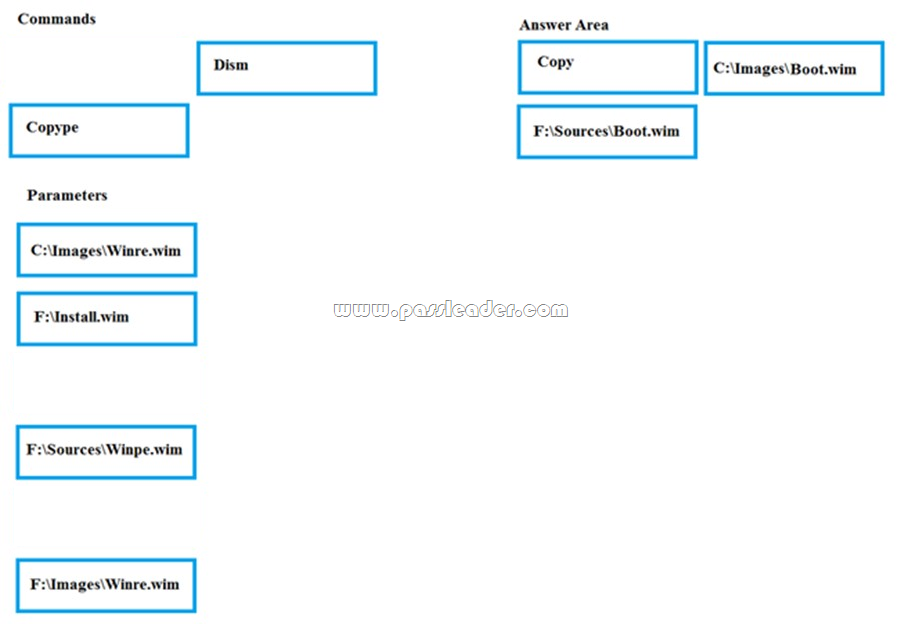
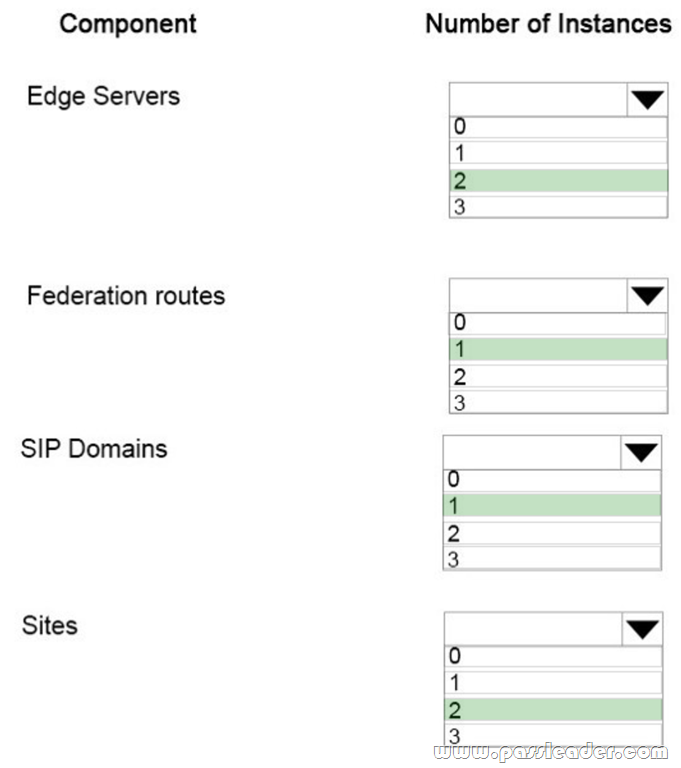
HotSpot
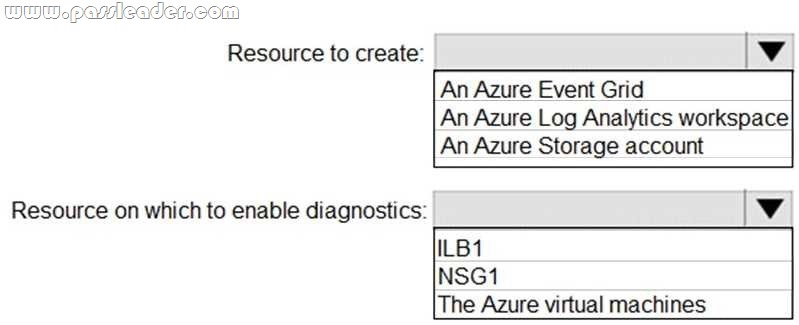
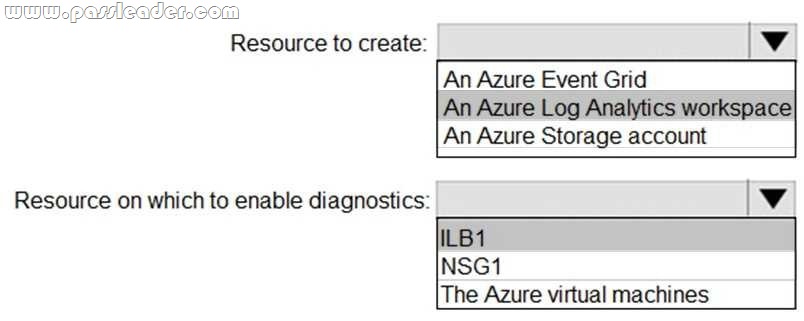
You have an Azure virtual network named VNet1 that connects to your on-premises network by using a site-to-site VPN. VNet1 contains one subnet named Subnet1. Subnet1 is associated to a network security group (NSG) named NSG1. Subnet1 contains a basic internal load balancer named ILB1. ILB1 has three Azure virtual machines in the backend pool. You need to collect data about the IP addresses that connects to ILB1. You must be able to run interactive queries from the Azure portal against the collected data. What should you do? (To answer, select the appropriate options in the answer area.)
![]()
Answer:
![]()
Explanation:
For Box 1: In the Azure portal you can set up a Log Analytics workspace, which is a unique Log Analytics environment with its own data repository, data sources, and solutions.
https://docs.microsoft.com/en-us/azure/azure-monitor/learn/quick-create-workspace
https://docs.microsoft.com/en-us/azure/load-balancer/load-balancer-standard-diagnostics
NEW QUESTION 17
You have a Basic App Service plan named ASP1 that hosts an Azure App Service named App1. You need to configure a custom domain and enable backups for App1. What should you do first?
A. Configure a WebJob for App1.
B. Scale up ASP1.
C. Scale out ASP1.
D. Configure the application settings for App1.
Answer: D
NEW QUESTION 18
You have an Azure subscription named Subscription1 that contains an Azure virtual network named VNet1. VNet1 connects to your on-premises network by using Azure ExpressRoute. You need to connect VNet1 to the on-premises network by using a site-to-site VPN. The solution must minimize cost. Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. Create a local site VPN gateway.
B. Create a VPN gateway that uses the VpnGw1 SKU.
C. Create a VPN gateway that uses the Basic SKU.
D. Create a gateway subnet.
E. Create a connection.
Answer: ABE
Explanation:
For a site to site VPN, you need a local gateway, a gateway subnet, a VPN gateway, and a connection to connect the local gateway and the VPN gateway. That would be four answers in this question. However, the question states that VNet1 connects to your on-premises network by using Azure ExpressRoute. For an ExpressRoute connection, VNET1 must already be configured with a gateway subnet so we don’t need another one.
NEW QUESTION 19
You are configuring Azure Active Directory (AD) Privileged Identity Management. You need to provide a user named Admm1 with read access to a resource group named RG1 for only one month. The user role must be assigned immediately. What should you do?
A. Assign an active role.
B. Assign an eligible role.
C. Assign a permanently active role.
D. Create a custom role and a conditional access policy.
Answer: B
Explanation:
Azure AD Privileged Identity Management introduces the concept of an eligible admin. Eligible admins should be users that need privileged access now and then, but not all-day, every day. The role is inactive until the user needs access, then they complete an activation process and become an active admin for a predetermined amount of time.
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
NEW QUESTION 20
You have an Azure subscription named Subscription1 and two Azure Active Directory (Azure AD) tenants named Tenant1 and Tenant2. Subscnption1 is associated to Tenant1 Multi-factor authentication (MFA) is enabled for all the users in Tenant1. You need to enable MFA for the users in Tenant2. The solution must maintain MFA for Tenant1. What should you do first?
A. Transfer the administration of Subscription1 to a global administrator of Tenants.
B. Configure the MFA Server setting in Tenant1.
C. Create and link a subscription to Tenant2.
D. Change the directory for Subscription1.
Answer: C
NEW QUESTION 21
……
Case Study 1 – ADatum
ADatum Corporation is a financial company that has two main offices in New York and Los Angeles. ADatum has a subsidiary named Fabrikam, Inc. that shares the Los Angeles office. ADatum is conducting an initial deployment of Azure services to host new line-of-business applications and is preparing to migrate its existing on-premises workloads to Azure. ADatum uses Microsoft Exchange Online for email.
……
NEW QUESTION 201
You need to recommend an environment for the deployment of App1. What should you recommend?
A. A new App Service plan that uses the P3v2 pricing tier.
B. ASE1 and an App Service plan that uses the I1 pricing tier.
C. ASE1 and an App Service plan that uses the I3 pricing tier.
D. A new App Service plan that uses the S1 pricing tier.
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/app-service/environment/app-service-app-service-environment-control-inbound-traffic
NEW QUESTION 202
You need to configure AG1. What should you create?
A. a multi-site listener
B. a URL path-based routing rule
C. a basic listener
D. a basic routing rule
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/application-gateway/application-gateway-create-url-route-portal
NEW QUESTION 203
What should you create to configure AG2?
A. multi-site listeners
B. basic listeners
C. URL path-based routing rules
D. basic routing rules
E. an additional public IP address
Answer: A
Explanation:
You need to configure an Azure Application Gateway with multi-site listeners to direct different URLs to different pools.
https://docs.microsoft.com/en-us/azure/application-gateway/multiple-site-overview
NEW QUESTION 204
……
Case Study 2 – Contoso, Ltd. (A)
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York. The Montreal office has 2,000 employees. The Seattle office has 1,000 employees. The New York office has 200 employees. All the resources used by Contoso are hosted on-premises. Contoso creates a new Azure subscription. The Azure Active Directory (Azure AD) tenant uses a domain named contoso.onmicrosoft.com. The tenant uses the P1 pricing tier.
……
NEW QUESTION 221
You discover that VM3 does NOT meet the technical requirements. You need to verify whether the issue relates to the NSGs. What should you use?
A. Diagram in VNet1.
B. The security recommendations in Azure Advisor.
C. Diagnostic settings in Azure Monitor.
D. Diagnose and solve problems in Traffic Manager Profiles.
E. IP flow verify in Azure Network Watcher.
Answer: E
Explanation:
IP flow verify checks if a packet is allowed or denied to or from a virtual machine. The information consists of direction, protocol, local IP, remote IP, local port, and remote port. If the packet is denied by a security group, the name of the rule that denied the packet is returned. While any source or destination IP can be chosen, IP flow verify helps administrators quickly diagnose connectivity issues from or to the internet and from or to the on-premises environment.
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-ip-flow-verify-overview
NEW QUESTION 222
You need to meet the technical requirement for VM4. What should you create and configure?
A. an Azure Notification Hub
B. an Azure Event Hub
C. an Azure Logic App
D. an Azure Services Bus
Answer: B
Explanation:
You can start an automated logic app workflow when specific events happen in Azure resources or third-party resources. These resources can publish those events to an Azure event grid. In turn, the event grid pushes those events to subscribers that have queues, webhooks, or event hubs as endpoints. As a subscriber, your logic app can wait for those events from the event grid before running automated workflows to perform tasks – without you writing any code.
https://docs.microsoft.com/en-us/azure/event-grid/monitor-virtual-machine-changes-event-grid-logic-app
NEW QUESTION 223
You need to recommend a solution to automate the configuration for the finance department users. The solution must meet the technical requirements. What should you include in the recommended?
A. Azure AP B2C.
B. Azure AD Identity Protection.
C. An Azure logic app and the Microsoft Identity Management (MIM) client.
D. Dynamic groups and conditional access policies.
Answer: D
Explanation:
The recommendation is to use conditional access policies that can then be targeted to groups of users, specific applications, or other conditions.
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userstates
NEW QUESTION 224
……
Case Study 3 – Humongous Insurance
Humongous Insurance has a single-domain Active Directory forest named humongousinsurance.com. The functional level of the forest is Windows Server 2012. You recently provisioned an Azure Active Directory (Azure AD) tenant. Each office has a local data center that contains all the servers for that office. Each office has a dedicated connection to the Internet. Each office has several link load balancers that provide access to the servers.
……
NEW QUESTION 231
Which blade should you instruct the finance department auditors to use?
A. Partner information
B. Overview
C. Payment methods
D. Invoices
Answer: D
Explanation:
You can opt in and configure additional recipients to receive your Azure invoice in an email. This feature may not be available for certain subscriptions such as support offers, Enterprise Agreements, or Azure in Open.
https://docs.microsoft.com/en-us/azure/billing/billing-download-azure-invoice-daily-usage-date
NEW QUESTION 232
You need to prepare the environment to meet the authentication requirements. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Azure Active Directory (AD) Identity Protection and an Azure policy.
B. A Recovery Services vault and a backup policy.
C. An Azure Key Vault and an access policy.
D. An Azure Storage account and an access policy.
Answer: BD
Explanation:
D: Seamless SSO works with any method of cloud authentication – Password Hash Synchronization or Pass-through Authentication, and can be enabled via Azure AD Connect.
B: You can gradually roll out Seamless SSO to your users. You start by adding the following Azure AD URL to all or selected users’ Intranet zone settings by using Group Policy in Active Directory.
Incorrect:
Not A: Seamless SSO needs the user’s device to be domain-joined, but doesn’t need for the device to be Azure AD Joined.
Not C: Azure AD connect does not port 8080. It uses port 443.
Not E: Seamless SSO is not applicable to Active Directory Federation Services (ADFS).
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sso-quick-start
NEW QUESTION 233
You need to resolve the licensing issue before you attempt to assign the license again. What should you do?
A. From the Groups blade, invite the user accounts to a new group.
B. From the Profile blade, modify the usage location.
C. From the Directory role blade, modify the directory role.
Answer: B
Explanation:
License cannot be assigned to a user without a usage location specified.
NEW QUESTION 234
……
Case Study 4 – Contoso, Ltd. (B)
Contoso, Ltd. is a manufacturing company that has offices worldwide. Contoso works with partner organizations to bring products to market. Contoso products are manufactured by using blueprint files that the company authors and maintains. Currently, Contoso uses multiple types of servers for business operations, including the following:
……
NEW QUESTION 241
You need to meet the user requirement for Admin1. What should you do?
A. From the Subscriptions blade, select the subscription, and then modify the Properties.
B. From the Subscriptions blade, select the subscription, and then modify the Access control (IAM) settings.
C. From the Azure Active Directory blade, modify the Properties.
D. From the Azure Active Directory blade, modify the Groups.
Answer: A
Explanation:
Change the Service administrator for an Azure subscription.
– Sign in to Account Center as the Account administrator.
– Select a subscription.
– On the right side, select Edit subscription details.
https://docs.microsoft.com/en-us/azure/billing/billing-add-change-azure-subscription-administrator
NEW QUESTION 242
You need to move the blueprint files to Azure. What should you do?
A. Generate a shared access signature (SAS). Map a drive, and then copy the files by using File Explorer.
B. Use the Azure Import/Export service.
C. Generate an access key. Map a drive, and then copy the files by using File Explorer.
D. Use Azure Storage Explorer to copy the files.
Answer: D
Explanation:
Azure Storage Explorer is a free tool from Microsoft that allows you to work with Azure Storage data on Windows, macOS, and Linux. You can use it to upload and download data from Azure blob storage.
https://docs.microsoft.com/en-us/azure/machine-learning/team-data-science-process/move-data-to-azure-blob-using-azure-storage-explorer
NEW QUESTION 243
You need to recommend an identify solution that meets the technical requirements. What should you recommend?
A. federated single-on (SSO) and Active Directory Federation Services (AD FS)
B. password hash synchronization and single sign-on (SSO)
C. cloud-only user accounts
D. pass-through Authentication and single sign-on (SSO)
Answer: A
Explanation:
Active Directory Federation Services is a feature and web service in the Windows Server Operating System that allows sharing of identity information outside a company’s network.
https://www.sherweb.com/blog/office-365/active-directory-federation-services/
NEW QUESTION 244
……
More Lab/SIMULATION
……
Download the newest PassLeader AZ-103 dumps from passleader.com now! 100% Pass Guarantee!
AZ-103 PDF dumps & AZ-103 VCE dumps: https://www.passleader.com/az-103.html (250 Q&As) (New Questions Are 100% Available and Wrong Answers Have Been Corrected! Free VCE simulator!)
P.S. New AZ-103 dumps PDF: https://drive.google.com/open?id=1pcJSvWksUYfrmRT5Hy9xnh0iGBvW_sfq
P.S. New AZ-102 dumps PDF: https://drive.google.com/open?id=1HceOeaJ6TUh6408k3UU7gZb7aXGzzGb–