New Updated 70-774 Exam Questions from PassLeader 70-774 PDF dumps! Welcome to download the newest PassLeader 70-774 VCE dumps: https://www.passleader.com/70-774.html (67 Q&As)
Keywords: 70-774 exam dumps, 70-774 exam questions, 70-774 VCE dumps, 70-774 PDF dumps, 70-774 practice tests, 70-774 study guide, 70-774 braindumps, Perform Cloud Data Science with Azure Machine Learning Exam
P.S. New 70-774 dumps PDF: https://drive.google.com/open?id=1kasCFEWbbVbNGXhtQ5AfwMOgYaKryNdH (New Version)
>> New 70-775 dumps PDF: https://drive.google.com/open?id=16Ko6acR3bnZwYnl–najNi9hP740P3Xt (New Version)
>> New 70-776 dumps PDF: https://drive.google.com/open?id=1R1iVzArLOI8VIIsY-pYYTq5ktJzHBkJR (New Version)
>> New 70-777 dumps PDF: https://drive.google.com/open?id=11SXUNBuzhaRm0xitNcbMAEyV_EwDqhFO (New Version)
NEW QUESTION 46
You plan to use Azure platform tools to detect and analyze food items in smart refrigerators. To provide families with an integrated experience for grocery shopping and cooking, the refrigerators will connect to other smart appliances, such as stoves and microwave ovens, on a LAN. You plan to build an object recognition model by using the Microsoft Cognitive Toolkit. The object recognition model will receive input from the connected devices and send results to applications. The training data will be derived from more than 10 TB of images. You will convert the raw images to the sparse format. You need to ensure that a web service endpoint can receive image data and use an object recognition model to return the expected object and the confidence level of the model. The solution must minimize the effort required to generate the client code to access the web service. Which resource should you use?
A. The edX Data Science Learning Dashboard.
B. Azure Machine Learning Studio.
C. Cortana Intelligence Gallery.
D. The Data Science Virtual Machine.
Answer: B
Explanation:
There are two ways to add an endpoint to a Web service.
– Programmatically
– Through the Azure Machine Learning Web Services portal
Adding an endpoint using the Azure Machine Learning Web Services portal:
1. In Machine Learning Studio, on the left navigation column, click Web Services.
2. At the bottom of the Web service dashboard, click Manage endpoints. The Azure Machine Learning Web Services portal opens to the endpoints page for the Web service.
3. Click New.
4. Type a name and description for the new endpoint.
https://docs.microsoft.com/en-us/azure/machine-learning/studio/create-endpoint
NEW QUESTION 47
You plan to use Azure platform tools to detect and analyze food items in smart refrigerators. To provide families with an integrated experience for grocery shopping and cooking, the refrigerators will connect to other smart appliances, such as stoves and microwave ovens, on a LAN. You plan to build an object recognition model by using the Microsoft Cognitive Toolkit. The object recognition model will receive input from the connected devices and send results to applications. The training data will be derived from more than 10 TB of images. You will convert the raw images to the sparse format. You need to deploy a multiple-service solution that was developed already and published by other users in the Microsoft development community. What should you use?
A. The edX Data Science Learning Dashboard.
B. The Data Science Virtual Machine.
C. An Azure Machine Learning experiment.
D. Cortana Intelligence Gallery.
Answer: D
Explanation:
Azure AI Gallery enables our growing community of developers and data scientists to share their analytics solutions.
https://gallery.azure.ai/
NEW QUESTION 48
You process some data by using Azure Machine Learning Studio. You have an intermediate dataset. The dataset has a column that contains date values stored in a format of MM/DD/YYYY. You need to split the column into three separate columns by year, month, and day. Which module should you use?
A. Edit Metadata
B. Normalize Data
C. Clean Missing Data
D. Import Data
E. Execute Python Script
F. Clip Values
G. Tune Model Hyperparameters
H. Select Columns in Dataset
Answer: E
Explanation:
You can use Python code to create a new column.
Incorrect:
Not F: The Clip Values module in Azure Machine Learning Studio, is used to identify and optionally replace data values that are above or below a specified threshold.
https://docs.microsoft.com/en-us/azure/machine-learning/service/how-to-transform-data
NEW QUESTION 49
You need to transform the columns in a dataset. The resulting data must be mean centered and have a variance of 1. The solution must use a native module. Which module should you use?
A. Execute Python Script
B. Import Data
C. Edit Metadata
D. Select Columns in Dataset
E. Clean Missing Data
F. Tune Model Hyperparameters
G. Clip Values
H. Normalize Data
Answer: H
NEW QUESTION 50
You need to change a column name to a friendly name. The solution must use a native module. Which module should you use?
A. Execute Python Script
B. Import Data
C. Edit Metadata
D. Select Columns in Dataset
E. Clean Missing Data
F. Tune Model Hyperparameters
G. Clip Values
H. Normalize Data
Answer: D
Explanation:
https://docs.microsoft.com/en-us/azure/machine-learning/studio-module-reference/select-columns-in-dataset
NEW QUESTION 51
You have a dataset that contains a column named Column1. Some of the values in Column1 are empty. You need to replace the empty values by using probabilistic Principal Component Analysis (PCA). The solution must use a native module. Which module should you use?
A. Execute Python Script
B. Import Data
C. Edit Metadata
D. Select Columns in Dataset
E. Clean Missing Data
F. Tune Model Hyperparameters
G. Clip Values
H. Normalize Data
Answer: E
Explanation:
You can use the Clean Missing Data module in Azure Machine Learning Studio, to remove, replace, or infer missing values. This module supports multiple type of operations for “cleaning” missing values, including:
– Replacing missing values with a placeholder, mean, or other value
– Completely removing rows and columns that have missing values
– Inferring values based on statistical methods
You can choose to replace using Probabilistic PCA: Replaces the missing values by using a linear model that analyzes the correlations between the columns and estimates a low-dimensional approximation of the data, from which the full data is reconstructed.
https://docs.microsoft.com/en-us/azure/machine-learning/studio-module-reference/clean-missing-data
NEW QUESTION 52
You plan to create a predictive analytics solution for credit risk assessment and fraud prediction in Azure Machine Learning. The Machine Learning workspace for the solution will be shared with other users in your organization. You will add assets to projects and conduct experiments in the workspace. The experiments will be used for training models that will be published to provide scoring from web services. The experiment for fraud prediction will use Machine Learning modules and APIs to train the models and will predict probabilities in an Apache Hadoop ecosystem. You plan to share the Machine Learning workspace with the other users. You are evaluating whether to assign the User role or the Owner role to several of the users. Which three actions can be performed by the users who are assigned the User role? (Each correct answer presents a complete solution. Choose three.)
A. Create, open, modify, and delete datasets.
B. Create, open, modify, and delete experiments.
C. Invite users to the workspace.
D. Delete users from the workspace.
E. Create, open, modify, and delete web services.
F. Access notebooks.
Answer: ABE
Explanation:
Once a Machine Learning workspace is created, you can invite users to your workspace and share access to your workspace and all of its experiments. We support two roles of users:
* User – A workspace user can create, open, modify and delete datasets, experiments and web services in the workspace.
* Owner – An owner can invite, remove, and list users with access to the workspace, in addition to what a user can do. He/she also have access to Notebooks.
https://github.com/anthonychu/azure-content/blob/master/articles/machine-learning/machine-learning-create-workspace.md
NEW QUESTION 53
You plan to create a predictive analytics solution for credit risk assessment and fraud prediction in Azure Machine Learning. The Machine Learning workspace for the solution will be shared with other users in your organization. You will add assets to projects and conduct experiments in the workspace. The experiments will be used for training models that will be published to provide scoring from web services. The experiment for fraud prediction will use Machine Learning modules and APIs to train the models and will predict probabilities in an Apache Hadoop ecosystem. The users will use different data sources that follow a standard format. The users will receive results in a standard format by using the fraud prediction web service. The results will be saved to a location specified by the users. You need to provide the users with the ability to get results for different risk tolerances without affecting the calculation of the model. Which three modules should be configured to use the Web Service Parameters? (Each correct answer presents part of the solution. Choose three.)
A. Evaluate Model
B. Import Data
C. Select Columns in Dataset
D. Export Data
E. Time Series Anomaly Detection
Answer: ABD
Explanation:
A: from scenario: the experiment for fraud prediction will use Machine Learning modules and APIs to train the models and will predict probabilities in an Apache Hadoop ecosystem.
B and D: an Azure Machine Learning web service is created by publishing an experiment that contains modules with configurable parameters. In some cases, you may want to change the module behavior while the web service is running. Web Service Parameters allow you to do this task.
https://docs.microsoft.com/en-us/azure/machine-learning/studio/web-service-parameters
NEW QUESTION 54
You need to identify which columns are more predictive by using a statistical method. Which module should you use?
A. Filter Based Feature Selection
B. Principal Component Analysis
C. Group Data into Bins
D. Tune Model Hyperparameters
Answer: A
Explanation:
In machine learning and statistics, feature selection is the process of selecting a subset of relevant, useful features to use in building an analytical model. Feature selection helps narrow the field of data to the most valuable inputs. Narrowing the field of data helps reduce noise and improve training performance. Feature selection is an important tool in machine learning. Machine Learning Studio provides multiple methods for performing feature selection. Choose a feature selection method based on the type of data that you have, and the requirements of the statistical technique that’s applied.
https://docs.microsoft.com/en-us/azure/machine-learning/studio-module-reference/feature-selection-modules
NEW QUESTION 55
You are building a classification experiment in Azure Machine Learning. You need to ensure that you can use the Evaluate Model module in the experiment. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Connect the input of the Score Model modules to the output of the Evaluate Model module.
B. Connect the input of the Score Model modules to the output of the Train Model modules and the output Split Data modules.
C. Connect the output of the Score Model modules to the input of the Evaluate Model module.
D. Connect the output of the Score Model modules to the input of the Train Model modules and the input of the Split Data modules.
Answer: BC
Explanation:
– Use the training data
To evaluate a model, you must connect a dataset that contains a set of input columns and scores. If no other data is available, you can use your original dataset.
1. Connect the Scored dataset output of the Score Model to the input of Evaluate Model.
2. Click Evaluate Model module, and select Run selected to generate the evaluation scores.
– Use the testing data
A common scenario in machine learning is to separate your original data set into training and testing datasets, using the Split module, or the Partition and Sample module.
1. Connect the Scored dataset output of the Score Model to the input of Evaluate Model.
2. Connect the output of the Split Data module that contains the testing data to the right-hand input of Evaluate Model.
3. Click Evaluate Model module, and select Run selected to generate the evaluation scores.
https://docs.microsoft.com/en-us/azure/machine-learning/studio-module-reference/evaluate-model
NEW QUESTION 56
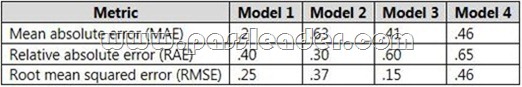
You are working on an Azure Machine Learning experiment that uses four different logistic regression algorithms. You are evaluating the algorithms based on the data in the following table:
![passleader-70-774-dumps-561_thumb passleader-70-774-dumps-561_thumb]()
Which model produces predictions that are the closest to the actual outcomes?
A. Model 1
B. Model 2
C. Model 3
D. Model 4
Answer: C
Explanation:
– Mean absolute error (MAE) measures how close the predictions are to the actual outcomes; thus, a lower score is better.
– Relative absolute error (RAE) is the relative absolute difference between expected and actual values; relative because the mean difference is divided by the arithmetic mean.
– Root mean squared error (RMSE) creates a single value that summarizes the error in the model. By squaring the difference, the metric disregards the difference between over-prediction and under-prediction.
https://docs.microsoft.com/en-us/azure/machine-learning/studio-module-reference/evaluate-model
NEW QUESTION 57
The manager of a call center reports that staffing the center is difficult because the number of calls is unpredictable. You have historical data that contains information about the calls. You need to build an Azure Machine Learning experiment to predict the number of total calls each hour. Which model should you use?
A. Multiclass Logistic Regression
B. Boosted Decision Tree Regression
C. Decision Forest Regression
D. Poisson Regression
Answer: D
Explanation:
Poisson regression is intended for use in regression models that are used to predict numeric values, typically counts. Therefore, you should use this module to create your regression model only if the values you are trying to predict fit the following conditions:
– The response variable has a Poisson distribution.
– Counts cannot be negative. The method will fail outright if you attempt to use it with negative labels.
– A Poisson distribution is a discrete distribution; therefore, it is not meaningful to use this method with non- whole numbers.
Incorrect:
Not A: Logistic regression is a well-known method in statistics that is used to predict the probability of an outcome, and is particularly popular for classification tasks. The algorithm predicts the probability of occurrence of an event by fitting data to a logistic function.
Not B: Boosting means that each tree is dependent on prior trees. The algorithm learns by fitting the residual of the trees that preceded it. Thus, boosting in a decision tree ensemble tends to improve accuracy with some small risk of less coverage.
Not C: Decision trees are non-parametric models that perform a sequence of simple tests for each instance, traversing a binary tree data structure until a leaf node (decision) is reached.
https://docs.microsoft.com/en-us/azure/machine-learning/studio-module-reference/poisson-regression
NEW QUESTION 58
You have an Apache Spark cluster in Azure HDInsight. The cluster includes 200 TB in five Apache Hive tables that have multiple foreign key relationships. You have an Azure Machine Learning model that was built by using SPARK Accelerated Failure Time (AFT) Survival Regression Model (spark.survreg). You need to prepare the Hive data into a single table as input for the Machine Learning model. The Hive data must be prepared in the least amount of time possible. What should you use to prepare the data?
A. A Hive user-defined function (UDF)
B. Spark SQL
C. The GPU
D. Java Mapreduce jobs
Answer: A
Explanation:
Create features for data in an HDInsight Hadoop cluster using Hive queries. Feature engineering attempts to increase the predictive power of learning algorithms by creating features from raw data that facilitate the learning process. You can run HiveQL queries from Azure ML, and access data processed in Hive and stored in blob storage, by using the Import Data module.
https://docs.microsoft.com/en-us/azure/hdinsight/hdinsight-machine-learning-overview#azure-machine-learning-and-hive
NEW QUESTION 59
You are building an Azure Machine Learning workflow by using Azure Machine Learning Studio. You create an Azure notebook that supports the Microsoft Cognitive Toolkit. You need to ensure that the stochastic gradient descent (SGD) configuration maximizes the samples per second and supports parallel modeling that is managed by a parameter server. Which SGD algorithm should you use?
A. DataParallelASGD
B. DataParallelSGD
C. BlockMomentumSGD
D. ModelAveragingSGD
Answer: A
Explanation:
Parameter server is a widely used framework in distributed machine learning. The most important benefit it brings is the asynchronous parallel training with many workers… you can use Data-Parallel ASGD.
Incorrect:
Not D: Model-Averaging SGD generally converges more slowly and to a worse optimum, compared to 1-bit SGD and Block-Momentum SGD, so it is no longer recommended.
https://docs.microsoft.com/en-us/cognitive-toolkit/multiple-gpus-and-machines
NEW QUESTION 60
You plan to use Azure Machine Learning to develop a predictive model. You plan to include an Execute Python Script module. What capability does the module provide?
A. importing Python modules from a ZIP file for execution in a Machine Learning experiment
B. performing interactive debugging of a Python script
C. saving the results of a Python script run in a Machine Learning environment to a local file
D. returning multiple data frames
Answer: A
Explanation:
A common use-case for many data scientists is to incorporate existing Python scripts into Azure ML experiments. Instead of requiring that all code be concatenated and pasted into a single script box, the Execute Python Script module accepts a zip file that contains Python modules at the third input port. The file is unzipped by the execution framework at runtime and the contents are added to the library path of the Python interpreter.
https://docs.microsoft.com/en-us/azure/machine-learning/studio/execute-python-scripts
NEW QUESTION 61
……
Download the newest PassLeader 70-774 dumps from passleader.com now! 100% Pass Guarantee!
70-774 PDF dumps & 70-774 VCE dumps: https://www.passleader.com/70-774.html (67 Q&As) (New Questions Are 100% Available and Wrong Answers Have Been Corrected! Free VCE simulator!)
P.S. New 70-774 dumps PDF: https://drive.google.com/open?id=1kasCFEWbbVbNGXhtQ5AfwMOgYaKryNdH (New Version)
>> New 70-775 dumps PDF: https://drive.google.com/open?id=16Ko6acR3bnZwYnl–najNi9hP740P3Xt (New Version)
>> New 70-776 dumps PDF: https://drive.google.com/open?id=1R1iVzArLOI8VIIsY-pYYTq5ktJzHBkJR (New Version)
>> New 70-777 dumps PDF: https://drive.google.com/open?id=11SXUNBuzhaRm0xitNcbMAEyV_EwDqhFO (New Version)








![passleader-pt0-001-dumps-841_thumb[3] passleader-pt0-001-dumps-841_thumb[3]](http://examgod.com/plimages/d1c91ab9eda0_9341/passleader-pt0-001-dumps-841_thumb3_thumb.png)