New Updated 400-201 Exam Questions from PassLeader 400-201 PDF dumps! Welcome to download the newest PassLeader 400-201 VCE dumps: https://www.passleader.com/400-201.html (951 Q&As)
Keywords: 400-201 exam dumps, 400-201 exam questions, 400-201 VCE dumps, 400-201 PDF dumps, 400-201 practice tests, 400-201 study guide, 400-201 braindumps, Cisco CCIE Service Provider Exam
P.S. New 400-201 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpVkYtTGdtRWFodXM
>> New CCIE Routing and Switching 400-101 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpfnRCUEFYcEhWZUw3OGNQY2FUSkptUXBrZDVzeE8zdkJQUERtOUFINDBFQW8
>> New CCIE Collaboration 400-051 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpNnliRG04bG9GbEk
>> New CCIE Data Center 400-151 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpVmo1Q01pZEhTUG8
>> New CCIE Security 400-251 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpd3JLalNVS0VWbms
>> New CCIE Wireless 400-351 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpWTFGcGFzN0JuYkE
NEW QUESTION 930
Which two components does the IS-IS IPv4 Loop-Free Alternate Fast Reroute feature fail to protect? (Choose two.)
A. ECMP
B. port channel
C. downstream path
D. subinterface
E. MPLS TE tunnels
Answer: DE
NEW QUESTION 931
Which three common use cases for customers using multiple cloud providers are true? (Choose three.)
A. bandwidth
B. high availability
C. feature disparity
D. security
E. analytics
F. regional cloud provider access
Answer: BCF
NEW QUESTION 932
Which statement describes the purpose of the EOBC links on an nV Edge solution using Cisco ASR 9000 Series?
A. synchronize control plane state information
B. provide backup transport of data plane traffic
C. prevent split-brain behavior in case of other link loss
D. provide primary transport of data plane traffic
Answer: A
NEW QUESTION 933
An engineer finds out that two LSRs do not reach an agreement on LDP neighborship session. Which mechanism prevents these two LSRs from engaging in an unthrottled sequence of session setup failures?
A. discovery transport-address
B. instance-tlv
C. LDP backoff
D. LCC
Answer: C
NEW QUESTION 934
BGP is used for PE-CE routing protocol and all CEs in the same VPN use the same AS number. Which command can be applied on PE router that eliminates the need to configure the AS override feature for the service provider in order to provide full connectivity amongst all CEs in the same VPN?
A. neighbor allowas-in
B. neighbor SoO
C. maximum-paths ibgp maximum-number
D. neighbor internal-vpn-client
Answer: A
NEW QUESTION 935
Which two statements about MPLS LDP Session Protection are true? (Choose two.)
A. LDP session protection can be applied onto to a directly connected neighbor.
B. LDP label bindings must be re-advertised when the directly connected link comes back.
C. LDP session stays up as long as the LDP peer is reachable after a network failure.
D. MPLS LDP session protection uses LDP targeted hellos.
E. MPLS LDP session protection and LDP IGP synchronization are mutually exclusive features.
Answer: CD
NEW QUESTION 936
OSPF is enabled on PE-to-CE links. To ensure that OSPF routes from CE routers are seen as OSPF interarea routes access the backbone, which type of configuration should be deployed on the PE routers?
A. the same domain ID value on both PE routers
B. down bit set for all LSA interarea
C. the same Site of Origin value on both PE routers
D. a sham link between PE routers
Answer: A
NEW QUESTION 937
During a failure, which BGP features forces subsecond convergence to an alternate path?
A. Prefix-Independent Convergence.
B. Aggressive BGP keepalive and holdtime timers.
C. Bidirectional Forwarding Detection.
D. BGP scanner timer reduced to minimal.
Answer: A
NEW QUESTION 938
An engineer has a requirement to implement OSPFv3 in such a way that modifying IP subnets within the domain does not affect the integrity of the SPF tree. Which specific LSA enables the engineer to avoid a forced SPF recalculation?
A. interarea prefix LSA
B. group membership LSA
C. intra-area prefix LSA
D. link LSA
Answer: C
NEW QUESTION 939
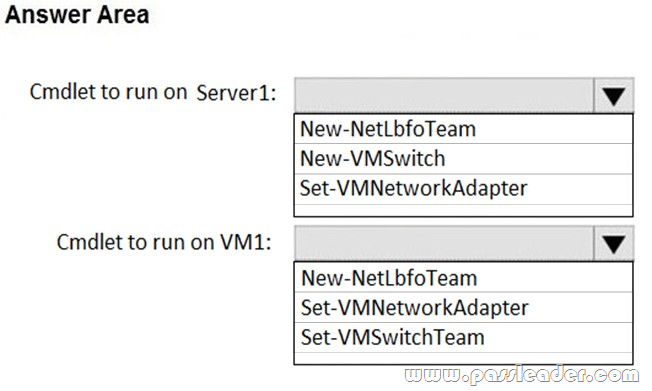
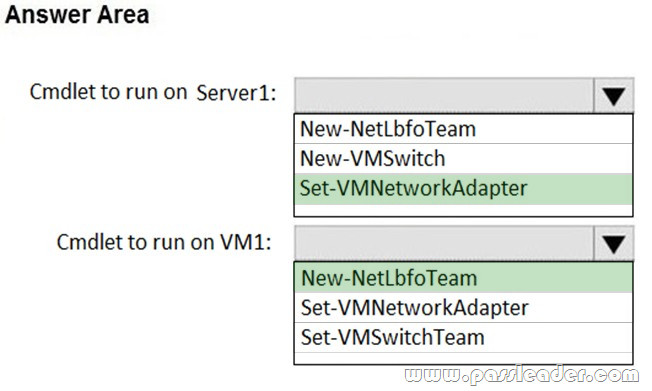
In which scenario can you host the most instances on a server?
A. using microservices application
B. using containers in virtual machines
C. using only containers
D. using only virtual machines
E. using virtual machines in containers
Answer: C
NEW QUESTION 940
Which two attributes about BFD are true? (Choose two.)
A. implemented only on route processors
B. increases the control plane CPU load
C. implemented on line cards
D. detects forwarding failures in milliseconds
E. more CPU intensive than routing protocol adjacency messages
Answer: CD
NEW QUESTION 941
The network operation center is receiving an excessive number of BFD alerts. This is due to recently configured high-speed links that result in BGP session teardown. Engineers tried to modify the BFD timers, but no improvement was noticed. Which action maximizes network stability?
A. enable the BFD Dampening feature
B. fully remove the BFD configuration
C. modify the IGP hello timers
D. enable the BGP Dampening feature
Answer: A
NEW QUESTION 942
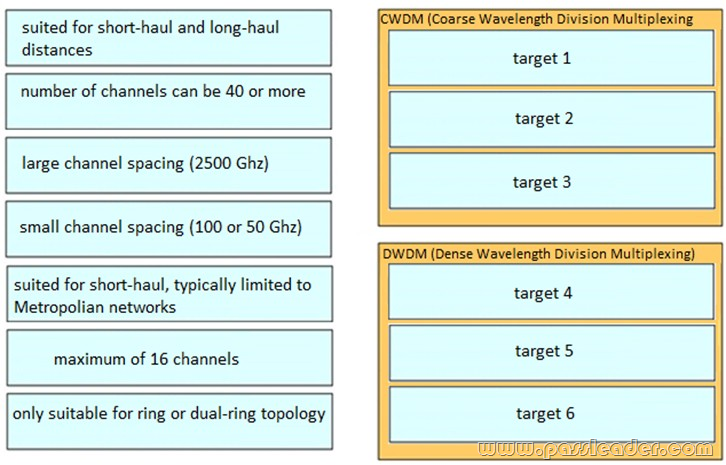
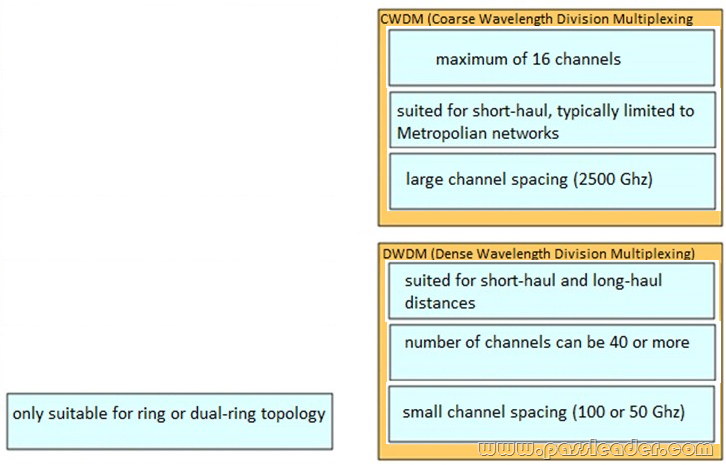
Which three parameters should be checked when you are troubleshooting DWDM technology? (Choose three.)
A. out-of-multiframe
B. signal-to-noise-ratio
C. loss of pointer
D. crosstalk
E. channel power
F. wavelength
Answer: ACF
NEW QUESTION 943
Which three PIM RP modes does IPv6 multicast support? (Choose three.)
A. BGP MDT
B. static RP
C. embedded RP
D. anycast RP
E. auto RP
F. BSR
Answer: BCF
NEW QUESTION 944
Which component is a correct G.8032 RPL type/node?
A. RPL peer node
B. RPL owner node
C. RPL uplink node
D. RPL next-peer node
Answer: B
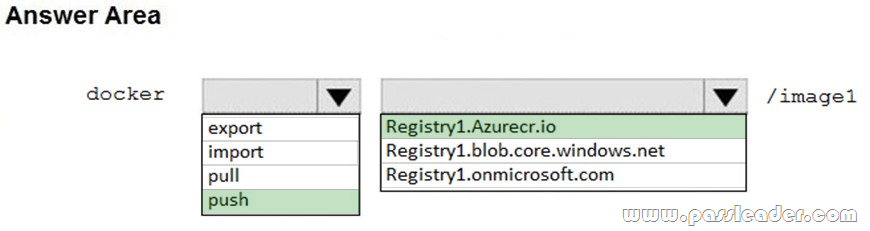
NEW QUESTION 945
Which description of SaaS is true?
A. a service offering a software environment in which applications can be build and deployed
B. a service offering on-demand software downloads
C. a service offering that allowing developers to build their own applications
D. a service offering on-demand licensed applications for end users
Answer: D
NEW QUESTION 946
Which MLDv1 message is the equivalent of the IGMP Leave message?
A. finish
B. leave
C. report
D. done
Answer: D
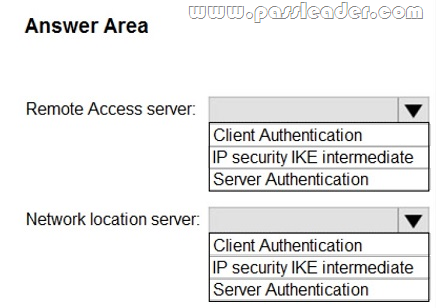
NEW QUESTION 947
An engineer needs to apply an SMU on a Cisco ASR 9000 device. Which high-availability capability minimize the impact of applying an SMU?
A. install activate
B. ISSU
C. graceful restart
D. NSF
E. NSR
Answer: B
NEW QUESTION 948
Which action enables an IPv6 multicast router on a subnet with locally attached receivers to quickly determine if there is a need to send traffic for a certain multicast group out to that subnet?
A. Adjust the MLD report interval on the router.
B. Activate IGPMv3 snooping and fast-leave.
C. Enable the MLDv2 explicit-tracking feature.
D. Decrease the ICMPv4 multicast query timer.
Answer: B
NEW QUESTION 949
Which three Layer 2 VPN pseudowire components are true? (Choose three.)
A. attachment circuit
B. bandwidth requirement
C. route distinguisher
D. virtual circuit label
E. pseudowire identifier
F. route target
Answer: ADE
NEW QUESTION 950
Which two protocols can be used for resilience in a Digital Building Ring topology? (Choose two.)
A. IS-IS
B. LLDP
C. REP
D. CDP
E. STP
Answer: CE
NEW QUESTION 951
……
Download the newest PassLeader 400-201 dumps from passleader.com now! 100% Pass Guarantee!
400-201 PDF dumps & 400-201 VCE dumps: https://www.passleader.com/400-201.html (951 Q&As) (New Questions Are 100% Available and Wrong Answers Have Been Corrected! Free VCE simulator!)
P.S. New 400-201 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpVkYtTGdtRWFodXM
>> New CCIE Routing and Switching 400-101 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpfnRCUEFYcEhWZUw3OGNQY2FUSkptUXBrZDVzeE8zdkJQUERtOUFINDBFQW8
>> New CCIE Collaboration 400-051 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpNnliRG04bG9GbEk
>> New CCIE Data Center 400-151 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpVmo1Q01pZEhTUG8
>> New CCIE Security 400-251 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpd3JLalNVS0VWbms
>> New CCIE Wireless 400-351 dumps PDF: https://drive.google.com/open?id=0B-ob6L_QjGLpWTFGcGFzN0JuYkE